The Internet Of Things
The Internet of things is the latest development in the long and continuing revolution of computing and communications. Its size, ubiquity, and influence on everyday lives, business, and government dwarf any technical advance that has gone before. This section provides a brief overview of the Internet of things.
物联网是计算和通信领域长期持续革命的最新发展。它的规模、无处不在以及对日常生活、商业和政府的影响使之前的任何技术进步都相形见绌。 本节简要介绍物联网。
Things on the Internet of Things
The Internet of things (IoT) is a term that refers to the expanding interconnection of smart devices, ranging from appliances to tiny sensors. A dominant theme is the embedding of short-range mobile transceivers into a wide array of gadgets and everyday items, enabling new forms of communication between people and things, and between things themselves. The Internet now supports the interconnection of billions of industrial and personal objects, usually through cloud systems. The objects deliver sensor information, act on their environment, and in some cases modify themselves, to create overall management of a larger system, like a factory or city.
The IoT is primarily driven by deeply embedded devices. These devices are lowbandwidth, low-repetition data capture, and low-bandwidth data-usage appliances that communicate with each other and provide data via user interfaces. Embedded appliances, such as high-resolution video security cameras, video VoIP phones, and a handful of others, require high-bandwidth streaming capabilities. Yet countless products simply require packets of data to be intermittently delivered.
物联网(IoT)是一个术语,指的是从家电到微型传感器等智能设备之间不断扩大的互联。一个主要的主题是将短程移动收发器嵌入到各种小工具和日常用品中,使人与物之间以及物与物之间的新形式的通信成为可能。互联网现在通常通过云系统支持数十亿工业和个人对象的互连。这些对象传递传感器信息,对其环境采取行动,并在某些情况下修改自己,以创建一个更大系统的整体管理,如工厂或城市。
物联网主要由深度嵌入式设备驱动。这些设备是低带宽、低重复数据捕获和低带宽数据使用设备,它们相互通信并通过用户界面提供数据。嵌入式设备,如高分辨率视频安全摄像机、视频VoIP电话和其他一些设备,需要高带宽流功能。然而,无数的产品只是要求数据包间歇性地传递。
Evolution
With reference to the end systems supported, the Internet has gone through roughly four generations of deployment culminating in the IoT:
-
Information technology: PCs, servers, routers, firewalls, and so on, bought as IT devices by enterprise IT people, primarily using wired connectivity.
-
Operational technology (OT): Machines/appliances with embedded IT built by non-IT companies, such as medical machinery, SCADA (supervisory control and data acquisition), process control, and kiosks, bought as appliances by enterprise OT people and primarily using wired connectivity.
- Personal technology: Smartphones, tablets, and eBook readers bought as IT devices by consumers (employees), exclusively using wireless connectivity and often multiple forms of wireless connectivity.
- Sensor/actuator technology: Single-purpose devices bought by consumers, IT, and OT people, exclusively using wireless connectivity, generally of a single form, as part of larger systems. The fourth generation is usually thought of as the IoT, and which is marked by using billions of embedded devices.
就支持的终端系统而言,互联网已经经历了大约四代的部署,最终形成了物联网:
信息技术:pc、服务器、路由器、防火墙等,由企业IT人员作为IT设备购买,主要使用有线连接。
操作技术(OT):由非IT公司制造的带有嵌入式IT的机器/设备,如医疗机械、SCADA(监控和数据采集)、过程控制和kiosks,由企业OT人员作为设备购买,主要使用有线连接。
- 个人技术:智能手机、平板电脑和电子书阅读器作为消费者(员工)购买的IT设备,专门使用无线连接,通常是多种形式的无线连接。
- 传感器/执行器技术:消费者、IT和OT人员购买的单一用途设备,专门使用无线连接,通常是单一形式,作为大型系统的一部分。 第四代通常被认为是物联网,其特点是使用数十亿个嵌入式设备。
Components of IoT-enabled Things
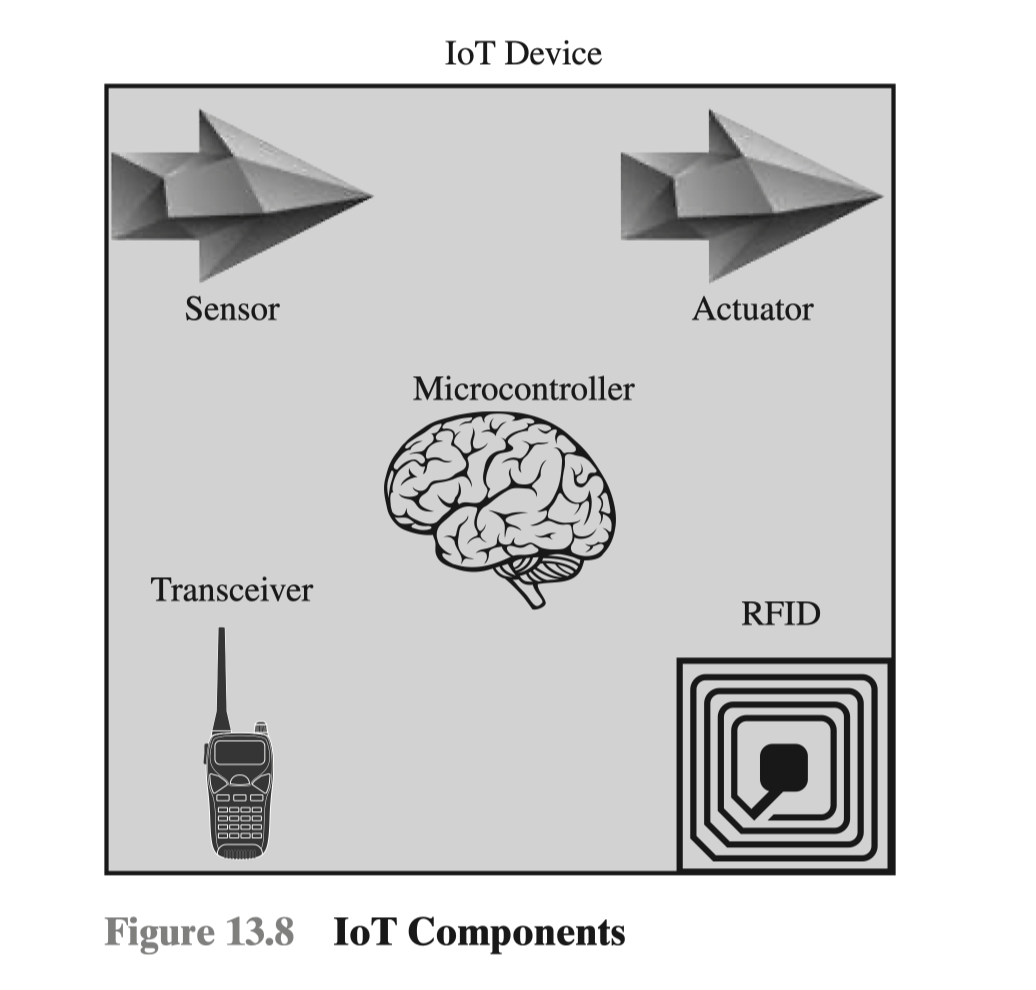
The key components of an IoT-enabled device are the following (see Figure 13.8):
-
Sensor: A sensor measures some parameter of a physical, chemical, or biological entity and delivers an electronic signal proportional to the observed characteristic, either in the form of an analog voltage level or a digital signal. In both cases, the sensor output is typically input to a microcontroller or other management element.
-
Actuator: An actuator receives an electronic signal from a controller and responds by interacting with its environment to produce an effect on some parameter of a physical, chemical, or biological entity.
-
Microcontroller: The “smart” in a smart device is provided by a deeply embedded microcontroller.
-
Transceiver: A transceiver contains the electronics needed to transmit and receive data. Most IoT devices contain a wireless transceiver, capable of communication using Wi-Fi, ZigBee, or some other wireless scheme.
-
Radio-frequency Identification (RFID): (RFID) technology, which uses radio waves to identify items, is increasingly becoming an enabling technology for IoT.
The main elements of an RFID system are tags and readers. RFID tags are small programmable devices used for object, animal, and human tracking. They come in a variety of shapes, sizes, functionalities, and costs. RFID readers acquire and sometimes rewrite information stored on RFID tags that come within operating range (a few inches up to several feet). Readers are usually connected to a computer system that records and formats the acquired information for further uses.
支持物联网的组件
支持物联网的设备的关键组件如下(见图13.8):
传感器: 传感器测量物理,化学或生物实体的某些参数,并以模拟电压电平或数字信号的形式提供与观察到的特性成比例的电子信号。在这两种情况下,传感器输出通常是微控制器或其他管理元件的输入。
致动器: 致动器接收来自控制器的电子信号,并通过与环境相互作用来响应,从而对物理,化学或生物实体的某些参数产生影响。
微控制器: 智能设备中的“智能”是由深度嵌入式微控制器提供的。
收发器: 收发器包含传输和接收数据所需的电子设备。大多数物联网设备都包含一个无线收发器,能够使用Wi-Fi、ZigBee或其他无线方案进行通信。
射频识别(RFID): 使用无线电波识别物品的RFID技术正日益成为物联网的使能技术。
RFID系统的主要元素是标签和读取器。RFID标签是用于跟踪物体、动物和人类的小型可编程设备。它们有各种形状、大小、功能和成本。RFID读取器获取并有时重写存储在操作范围内(几英寸到几英尺)的RFID标签上的信息。读卡器通常连接到一个计算机系统,该系统记录并格式化获取的信息以供进一步使用。
IoT and Cloud Context
To better understand the function of an IoT, it is useful to view it in the context of a complete enterprise network that includes third-party networking and cloud computing elements. Figure 13.9 provides an overview illustration.

EDGE At the edge of a typical enterprise network is a network of IoT-enabled devices, consisting of sensors and perhaps actuators. These devices may communicate with one another. For example, a cluster of sensors may all transmit their data to one sensor that aggregates the data to be collected by a higher-level entity. At this level, there may also be a number of gateways. A gateway interconnects the IoT-enabled devices with the higher-level communication networks. It performs the necessary translation between the protocols used in the communication networks and those used by devices. A gateway may also perform a basic data aggregation function.
FOG In many IoT deployments, massive amounts of data may be generated by a distributed network of sensors. For example, offshore oil fields and refineries can generate a terabyte of data per day. An airplane can create multiple terabytes of data per hour. Rather than store all of that data permanently (or at least for a long period) in central storage accessible to IoT applications, it is often desirable to do as much data processing close to the sensors as possible.
Thus, the purpose of what is sometimes referred to as the edge computing level is to convert network data flows into information that is suitable for storage and higher-level processing. Processing elements at these levels may deal with high volumes of data and perform data transformation operations, resulting in the storage of much lower volumes of data. The following are examples of fog computing operations:
- Evaluation: Evaluating data for criteria as to whether it should be processed at a higher level.
- Formatting: Reformatting data for consistent higher-level processing.
- Expanding/decoding: Handling cryptic data with additional context (such as the origin).
- Distillation/reduction: Reducing and/or summarizing data to minimize the impact of data and traffic on the network and higher-level processing systems.
- Assessment: Determining whether data represent a threshold or alert; this could include redirecting data to additional destinations
Generally, fog computing devices are deployed physically near the edge of the IoT network; that is, near the sensors and other data-generating devices. Thus, some of the basic processing of large volumes of generated data is offloaded and outsourced from IoT application software located at the center of the network.
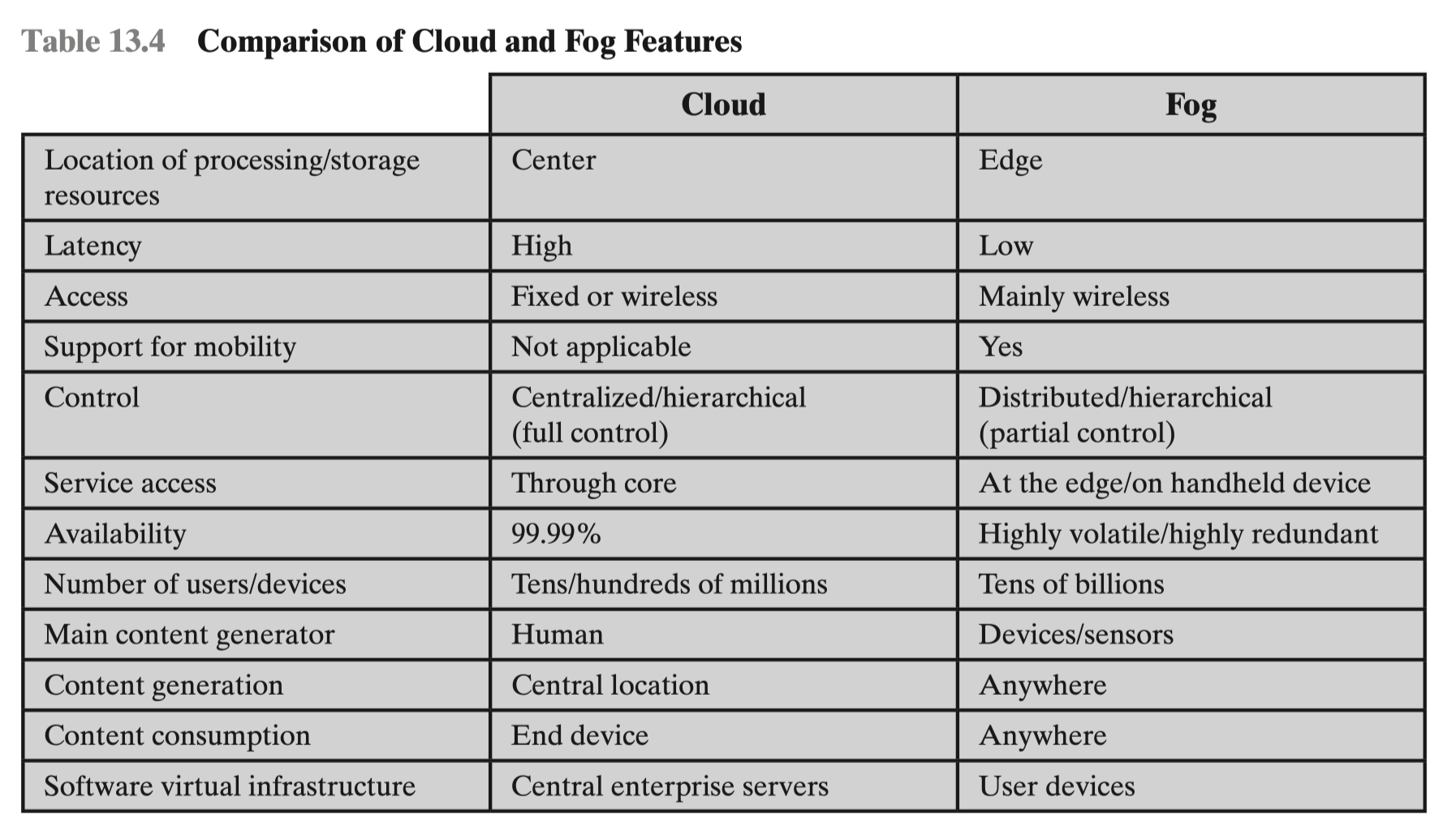
Fog computing and fog services are becoming a distinguishing characteristic of the IoT. Fog computing represents an opposite trend in modern networking from cloud computing. With cloud computing, massive, centralized storage and processing resources are made available to distributed customers over cloud networking facilities to a relatively small number of users. With fog computing, massive numbers of individual smart objects are interconnected with fog networking facilities that provide processing and storage resources close to the edge devices in an IoT. Fog computing addresses the challenges raised by the activity of thousand or millions of smart devices, including security, privacy, network capacity constraints, and latency requirements. The term fog computing is inspired by the fact that fog tends to hover low to the ground, whereas clouds are high in the sky.
CORE The core network, also referred to as a backbone network, connects geographically dispersed fog networks as well as provides access to other networks that are not part of the enterprise network. Typically, the core network will use very high performance routers, high-capacity transmission lines, and multiple interconnected routers for increased redundancy and capacity. The core network may also connect to high-performance, high-capacity servers, such as large database servers and private cloud facilities. Some of the core routers may be purely internal, providing redundancy and additional capacity without serving as edge routers.
CLOUD The cloud network provides storage and processing capabilities for the massive amounts of aggregated data that originate in IoT-enabled devices at the edge. Cloud servers also host the applications that (1) interact with and manage the IoT devices, and (2) analyze the IoT-generated data. Table 13.4 compares cloud and fog computing.
物联网和云环境
为了更好地理解物联网的功能,将其放在一个完整的企业网络中(包括第三方网络和云计算元素)是很有用的。图13.9提供了一个概览说明。
EDGE典型企业网络的边缘是支持物联网的设备网络,由传感器和执行器组成。这些设备可以相互通信。例如,一组传感器可能都将它们的数据传输到一个传感器,该传感器将由更高级别的实体收集的数据聚合在一起。在这个级别上,也可能有许多网关。网关将支持物联网的设备与更高级的通信网络连接起来。它在通信网络中使用的协议和设备使用的协议之间执行必要的转换。网关还可以执行基本的数据聚合功能。
在许多物联网部署中,大量数据可能由分布式传感器网络生成。例如,海上油田和炼油厂每天可以产生1tb的数据。一架飞机每小时可以产生数tb的数据。与其将所有数据永久(或至少长时间)存储在物联网应用程序可访问的中央存储中,不如尽可能多地在靠近传感器的地方进行数据处理。
因此,有时被称为边缘计算层的目的是将网络数据流转换为适合存储和更高级处理的信息。这些级别的处理元素可能处理大量数据并执行数据转换操作,从而导致存储的数据量大大减少。以下是雾计算操作的示例:
- 评价:根据是否应在更高一级处理的标准评价数据。
- 格式化:重新格式化数据以获得一致的高级处理。
- 扩展/解码:处理带有附加上下文(如来源)的神秘数据。
- 蒸馏/减少:减少和/或汇总数据,以尽量减少数据和流量对网络和高级处理系统的影响。
- 评估:确定数据是否代表阈值或警报;这可能包括将数据重定向到其他目的地
通常,雾计算设备物理上部署在物联网网络的边缘附近;也就是说,靠近传感器和其他数据生成设备。因此,对大量生成数据的一些基本处理被卸载并外包给位于网络中心的物联网应用软件。
雾计算和雾服务正在成为物联网的显著特征。雾计算代表了与云计算相反的现代网络趋势。有了云计算,大量的、集中的存储和处理资源可以通过云网络设施提供给分布的客户,而用户数量相对较少。通过雾计算,大量单个智能对象与雾网络设施互联,雾网络设施提供接近物联网边缘设备的处理和存储资源。雾计算解决了数千或数百万智能设备的活动所带来的挑战,包括安全性、隐私性、网络容量限制和延迟需求。雾计算这个术语的灵感来自于这样一个事实,即雾往往徘徊在离地面较低的地方,而云则在天空较高的地方。
核心网,也称为骨干网,连接地理上分散的雾网,并提供对不属于企业网络的其他网络的访问。通常,核心网络将使用高性能路由器、高容量传输线和多个互连路由器,以增加冗余和容量。核心网络还可以连接到高性能、高容量的服务器,例如大型数据库服务器和私有云设施。一些核心路由器可能纯粹是内部的,提供冗余和额外的容量,而不充当边缘路由器。
云网络为源自边缘物联网设备的大量聚合数据提供存储和处理能力。云服务器还托管应用程序(1)与物联网设备交互和管理,以及(2)分析物联网生成的数据。表13.4对云和雾计算的比较。
13.5 IOT SECURITY

IoT is perhaps the most complex and undeveloped area of network security. To see this, consider Figure 13.10, which shows the main elements of interest for IoT security. At the center of the network are the application platforms, data storage servers, and network and security management systems. These central systems gather data from sensors, send control signals to actuators, and are responsible for managing the IoT devices and their communication networks. At the edge of the network are IoT-enabled devices, some of which are quite simple constrained devices, and some of which are more intelligent unconstrained devices. As well, gateways may perform protocol conversion and other networking service on behalf of IoT devices.
Figure 13.10 illustrates a number of typical scenarios for interconnection and the inclusion of security features. The shading in Figure 13.10 indicates the systems that support at least some of these functions. Typically, gateways will implement secure functions, such as TLS and IPsec. Unconstrained devices may or may not implement some security capability. Constrained devices generally have limited or no security features. As suggested in the figure, gateway devices can provide secure communication between the gateway and the devices at the center, such as application platforms and management platforms. However, any constrained or unconstrained devices attached to the gateway are outside the zone of security established between the gateway and the central systems. As shown, unconstrained devices can communicate directly with the center and support security functions. However, constrained devices that are not connected to gateways have no secure communications with central devices.
物联网可能是网络安全中最复杂、最未开发的领域。要了解这一点,请考虑图13.10,其中显示了物联网安全感兴趣的主要元素。网络的核心是应用平台、数据存储服务器、网络和安全管理系统。这些中央系统从传感器收集数据,向执行器发送控制信号,并负责管理物联网设备及其通信网络。在网络的边缘是支持物联网的设备,其中一些是非常简单的受限设备,其中一些是更智能的无约束设备。网关也可以代表物联网设备执行协议转换和其他网络服务。
图13.10展示了互连和包含安全特性的一些典型场景。图13.10中的阴影表示至少支持其中一些功能的系统。通常,网关将实现安全功能,如TLS和IPsec。不受约束的设备可能实现也可能不实现某些安全功能。受约束的设备通常具有有限或没有安全特性。如图所示,网关设备可以提供网关与中心设备(如应用平台、管理平台)之间的安全通信。但是,连接到网关的任何受约束或不受约束的设备都在网关和中央系统之间建立的安全区域之外。如图所示,不受约束的设备可以直接与中心通信,并支持安全功能。但是,未连接到网关的受约束设备无法与中心设备进行安全通信。
The Patching Vulnerability
In an often-quoted 2014 article, security expert Bruce Schneier stated that we are at a crisis point with regard to the security of embedded systems, including IoT devices [SCHN14]. The embedded devices are riddled with vulnerabilities and there is no good way to patch them. The chip manufacturers have strong incentives to produce their product with its firmware and software as quickly and cheaply as possible. The device manufacturers choose a chip based on price and features and do very little if anything to the chip software and firmware. Their focus is the functionality of the device itself. The end user may have no means of patching the system or, if so, little information about when and how to patch. The result is that the hundreds of millions of Internet-connected devices in the IoT are vulnerable to attack. This is certainly a problem with sensors, allowing attackers to insert false data into the network. It is potentially a graver threat with actuators, where the attacker can affect the operation of machinery and other devices.
在2014年一篇经常被引用的文章中,安全专家Bruce Schneier指出,我们正处于嵌入式系统(包括物联网设备)安全的危机点。嵌入式设备漏洞百出,没有好的方法来修补它们。芯片制造商有强烈的动机,以尽可能快和便宜的价格生产带有该公司固件和软件的产品。设备制造商根据价格和功能来选择芯片,对芯片的软件和固件几乎不做任何改动。他们关注的是设备本身的功能。最终用户可能没有办法给系统打补丁,或者如果有的话,关于何时以及如何打补丁的信息也很少。其结果是,物联网中数以亿计的互联网连接设备很容易受到攻击。这当然是传感器的一个问题,允许攻击者将虚假数据插入网络。对于执行器来说,这可能是一个更严重的威胁,攻击者可以影响机械和其他设备的运行。
IoT Security and Privacy Requirements Defined by ITU-T
ITU-T Recommendation Y.2066 (Common Requirements of the Internet of Things, June 2014) includes a list of security requirements for the IoT. This list is a useful baseline for understanding the scope of security implementation needed for an IoT deployment. The requirements are defined as being the functional requirements during capturing, storing, transferring, aggregating, and processing the data of things, as well as to the provision of services which involve things. These requirements are related to all the IoT actors. The requirements are the following:
- Communication security: Secure, trusted, and privacy protected communication capability is required, so unauthorized access to the content of data can be prohibited, integrity of data can be guaranteed and privacy-related content of data can be protected during data transmission or transfer in IoT.
- Data management security: Secure, trusted, and privacy protected data management capability is required, so unauthorized access to the content of data can be prohibited, integrity of data can be guaranteed, and privacy-related content of data can be protected when storing or processing data in IoT.
- Service provision security: Secure, trusted, and privacy protected service provision capability is required, so unauthorized access to service and fraudulent service provision can be prohibited and privacy information related to IoT users can be protected.
- Integration of security policies and techniques: The ability to integrate different security policies and techniques is required, so as to ensure a consistent security control over the variety of devices and user networks in IoT.
- Mutual authentication and authorization: Before a device (or an IoT user) can access the IoT, mutual authentication and authorization between the device (or the IoT user) and IoT is required to be performed according to predefined security policies.
- Security audit: Security audit is required to be supported in IoT. Any data access or attempt to access IoT applications are required to be fully transparent, traceable and reproducible according to appropriate regulation and laws. In particular, IoT is required to support security audit for data transmission, storage, processing, and application access.
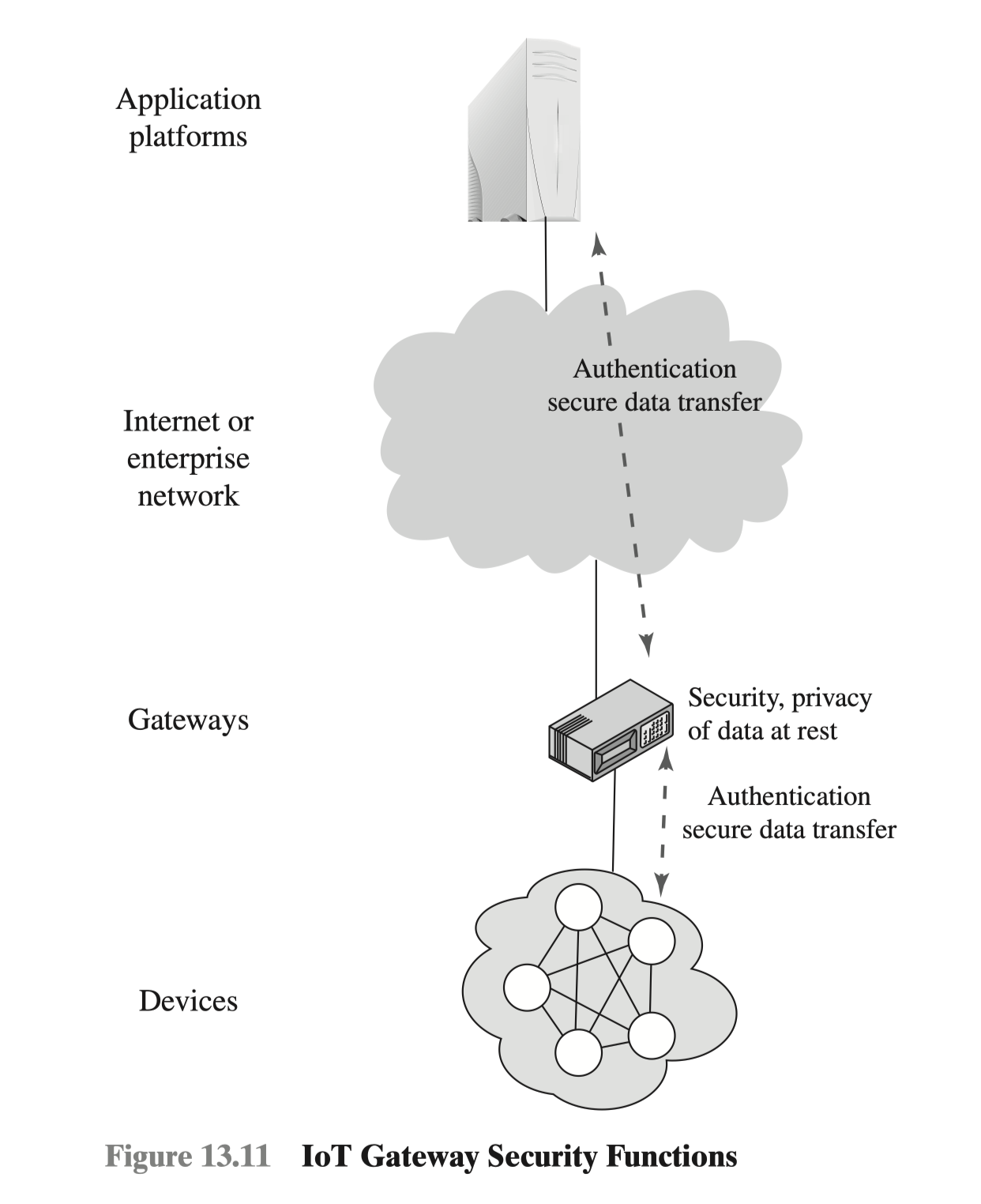
A key element in providing security in an IoT deployment is the gateway. ITU-T Recommendation Y.2067 (Common Requirements and Capabilities of a Gateway for Internet of Things Applications, June 2014) details specific security functions that the gateway should implement, some of which are illustrated in Figure 13.11. These consist of the following:
Support identification of each access to the connected devices.
- Support authentication with devices. Based on application requirements and device capabilities, it is required to support mutual or one-way authentication with devices. With one-way authentication, either the device authenticates itself to the gateway or the gateway authenticates itself to the device, but not both.
- Support mutual authentication with applications.
- Support the security of the data that are stored in devices and the gateway, or transferred between the gateway and devices, or transferred between the gateway and applications. Support the security of these data based on security levels.
- Support mechanisms to protect privacy for devices and the gateway.
- Support self-diagnosis and self-repair as well as remote maintenance.
- Support firmware and software update.
- Support auto configuration or configuration by applications. The gateway is required to support multiple configuration modes, for example, remote and local configuration, automatic and manual configuration, and dynamic configuration based on policies.
Some of these requirements may be difficult to achieve when they involve providing security services for constrained devices. For example, the gateway should support security of data stored in devices. Without encryption capability at the constrained device, this may be impractical to achieve.
Note the Y.2067 requirements make a number of references to privacy requirements. Privacy is an area of growing concern with the widespread deployment of IoT-enabled things in homes, retail outlets, and vehicles and humans. As more things are interconnected, governments and private enterprises will collect massive amounts of data about individuals, including medical information, location and movement information, and application usage.
ITU-T定义的物联网安全和隐私要求
ITU-T建议Y.2066(物联网通用要求,2014年6月)包含物联网安全要求列表。此列表是了解物联网部署所需的安全实施范围的有用基准。需求被定义为在获取、存储、传输、聚合和处理物的数据过程中的功能需求,以及对涉及物的服务的提供。这些需求与所有物联网参与者相关。具体要求如下:
- 通信安全:需要安全、可信、保护隐私的通信能力,在物联网的数据传输或传输过程中,可以禁止对数据内容的未经授权的访问,保证数据的完整性,保护与隐私相关的数据内容。
- 数据管理安全:需要安全、可信、保护隐私的数据管理能力,在物联网中存储或处理数据时,可以禁止对数据内容的未经授权访问,保证数据的完整性,保护与隐私相关的数据内容。
- 服务提供安全:需要安全、可信、保护隐私的服务提供能力,防止未经授权访问服务和欺诈提供服务,保护物联网用户的隐私信息。
- 安全策略和技术的集成:需要具备不同安全策略和技术的集成能力,以确保对物联网中各种设备和用户网络的一致安全控制。
- 相互认证授权:在设备(或物联网用户)接入物联网之前,需要设备(或物联网用户)与物联网之间按照预定义的安全策略进行相互认证授权。
- 安全审计:物联网需要支持安全审计。根据适当的法规和法律,任何数据访问或尝试访问物联网应用程序都需要完全透明、可追溯和可复制。 特别是,物联网需要支持对数据传输、存储、处理和应用访问的安全审计。
在物联网部署中提供安全性的一个关键因素是网关。ITU-T建议Y.2067(物联网应用网关的通用要求和功能,2014年6月)详细介绍了网关应实现的具体安全功能,其中一些功能如图13.11所示。这些措施包括:
支持对连接设备的每次访问进行识别。
- 支持设备认证。根据应用需求和设备功能,需要支持与设备之间的双向或单向身份验证。使用单向身份验证时,要么设备向网关验证自己,要么网关向设备验证自己,但不能同时验证两者。
- 支持应用程序之间的相互认证。
- 支持存储在设备和网关之间、网关和设备之间、网关和应用之间的数据的安全性。根据安全级别支持这些数据的安全性。
支持保护设备和网关隐私的机制。
支持自诊断、自修复和远程维护。
- 支持固件和软件更新。
- 支持自动配置或应用程序配置。要求网关支持多种配置方式,如远程配置和本地配置、自动配置和手动配置、基于策略的动态配置等。
当涉及到为受限设备提供安全服务时,其中一些要求可能难以实现。例如,网关应支持存储在设备中的数据的安全性。如果在受约束的设备上没有加密功能,这可能是不切实际的。
请注意,Y.2067要求多次提到隐私要求。随着物联网设备在家庭、零售店、车辆和人类中的广泛部署,隐私问题日益受到关注。随着越来越多的事物相互关联,政府和私营企业将收集大量关于个人的数据,包括医疗信息、位置和运动信息以及应用程序使用情况。
An IoT Security Framework
Cisco has developed a framework for IoT security [FRAH15] that serves as a useful guide to the security requirements for IoT. Figure 13.12 illustrates the security environment related to the logical structure of an IoT. The IoT model is a simplified version of the World Forum IoT Reference Model. It consists of the following levels:
- Smart objects/embedded systems: Consists of sensors, actuators, and other embedded systems at the edge of the network. This is the most vulnerable part of an IoT. The devices may not be in a physically secure environment and may need to function for years. Availability is certainly an issue. Network managers also need to be concerned about the authenticity and integrity of the data generated by sensors and about protecting actuators and other smart devices from unauthorized use. Privacy and protection from eavesdropping may also be requirements.
- Fog/edge network: This level is concerned with the wired and wireless interconnection of IoT devices. In addition, a certain amount of data processing and consolidation may be done at this level. A key issue of concern is the wide variety of network technologies and protocols used by the various IoT devices and the need to develop and enforce a uniform security policy.
- Core network: The core network level provides data paths between network center platforms and the IoT devices. The security issues here are those confronted in traditional core networks. However, the vast number of endpoints to interact with and manage creates a substantial security burden.
- Data center/cloud: This level contains the application, data storage, and network management platforms. IoT does not introduce any new security issues at this level, other than the necessity of dealing with huge numbers of individual endpoints. Within this four-level architecture, the Cisco model defines four general security capabilities that span multiple levels:
- Role-based security: RBAC systems assign access rights to roles instead of individual users. In turn, users are assigned to different roles, either statically
- or dynamically, according to their responsibilities. RBAC enjoys widespread commercial use in cloud and enterprise systems and is a well-understood tool that can be used to manage access to IoT devices and the data they generate.
- Anti-tamper and detection: This function is particularly important at the device and fog network levels but also extends to the core network level. All of these levels may involve components that are physically outside the area of the enterprise that is protected by physical security measures.
- Data protection and confidentiality: These functions extend to all level of the architecture.
- Internet protocol protection: Protection of data in motion from eavesdropping and snooping is essential between all levels.
Figure 13.12 maps specific security functional areas across the four layers of the IoT model. [FRAH15] also proposes a secure IoT framework that defines the components of a security facility for an IoT that encompasses all the levels, as shown in Figure 13.13. The four components are:

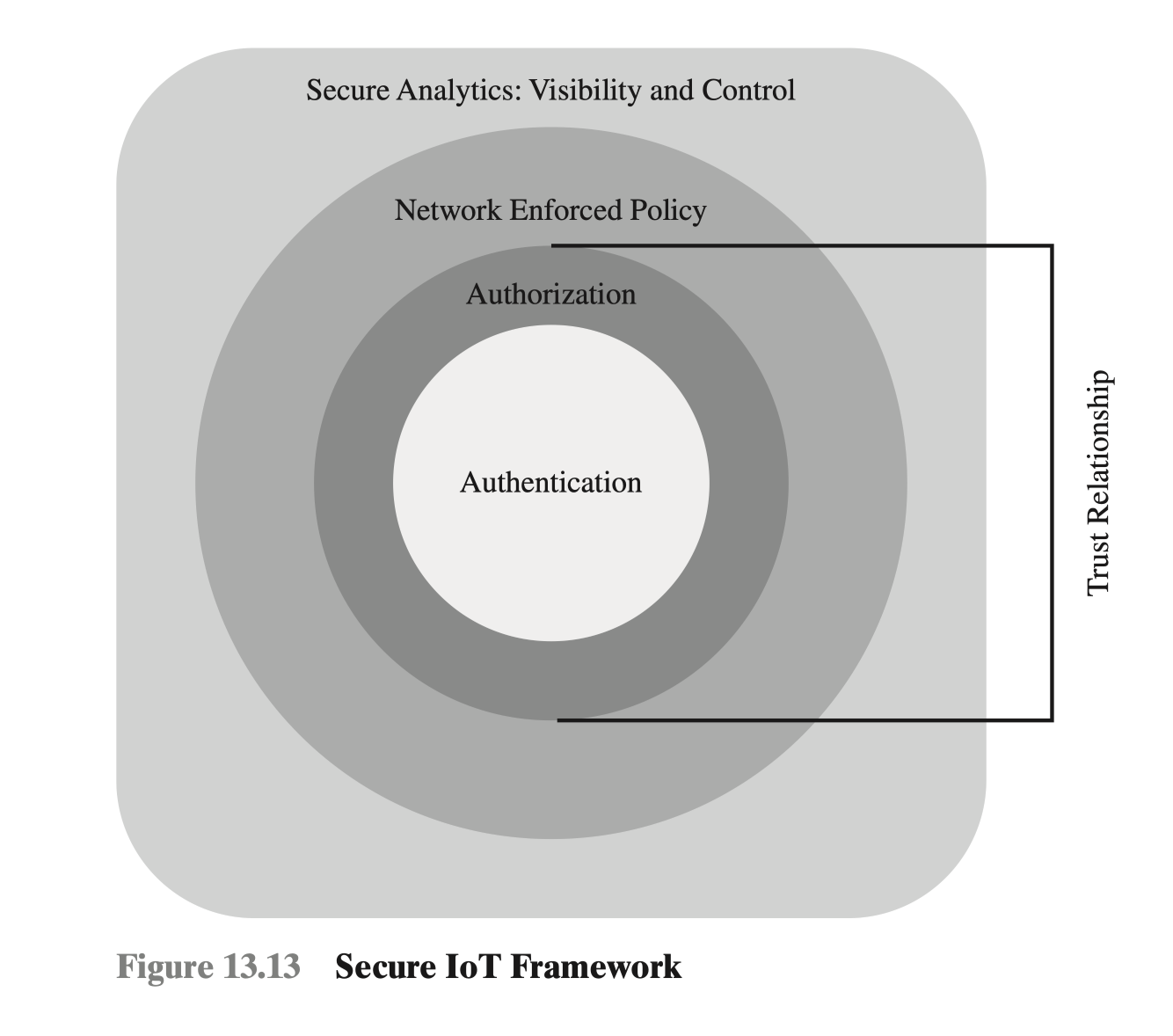
- Authentication: Encompasses the elements that initiate the determination of access by first identifying the IoT devices. In contrast to typical enterprise network devices, which may be identified by a human credential (e.g., username and password or token), the IoT endpoints must be fingerprinted by means that do not require human interaction. Such identifiers include RFID, x.509 certificates, or the MAC address of the endpoint.
- Authorization: Controls a device’s access throughout the network fabric. This element encompasses access control. Together with the authentication layer, it establishes the necessary parameters to enable the exchange of information between devices and between devices and application platforms and enables IoT-related services to be performed.
- Network enforced policy: Encompasses all elements that route and transport endpoint traffic securely over the infrastructure, whether control, management, or actual data traffic.
- Secure analytics, including visibility and control: This component includes all the functions required for central management of IoT devices. This involves, firstly, visibility of IoT devices, which simply means that central management services are securely aware of the distributed IoT device collection, including identity and attributes of each device. Building on this visibility is the ability to exert control, including configuration, patch updates, and threat countermeasures.
An important concept related to this framework is that of trust relationship. In this context, trust relationship refers to the ability of the two partners to an exchange to have confidence in the identity and access rights of the other. The authentication component of the trust framework provides a basic level of trust, which is expanded with the authorization component. [FRAH15] gives the example that a car may establish a trust relationship with another car from the same vendor. That trust relationship, however, may only allow cars to exchange their safety capabilities. When a trusted relationship is established between the same car and its dealer’s network, the car may be allowed to share additional information such as its odometer reading and last maintenance record.
物联网安全框架
思科已经开发了一个物联网安全框架[FRAH15],作为物联网安全需求的有用指南。物联网逻辑结构相关的安全环境如图13.12所示。物联网模型是世界论坛物联网参考模型的简化版本。它由以下几个层次组成:
- 智能对象/嵌入式系统:由传感器、执行器和网络边缘的其他嵌入式系统组成。这是物联网中最脆弱的部分。这些设备可能不在物理安全的环境中,可能需要运行多年。可用性当然是个问题。网络管理人员还需要关注传感器生成数据的真实性和完整性,以及保护执行器和其他智能设备免受未经授权的使用。隐私和防止窃听也可能是要求。
- 雾/边缘网络:该级别涉及物联网设备的有线和无线互连。此外,一定数量的数据处理和整合可以在此级别完成。关注的一个关键问题是各种物联网设备使用的各种网络技术和协议,以及开发和执行统一安全策略的需求。
- 核心网:核心网层提供网络中心平台与物联网设备之间的数据路径。这里的安全问题是传统核心网所面临的问题。然而,要与之交互和管理的大量端点造成了巨大的安全负担。
- 数据中心/云:该级别包含应用程序、数据存储和网络管理平台。除了需要处理大量的单个端点之外,物联网在这个级别上没有引入任何新的安全问题。 在这个四层架构中,思科模型定义了四个跨越多个级别的通用安全功能:
- 基于角色的安全性:RBAC系统将访问权限分配给角色而不是单个用户。反过来,用户被静态地分配到不同的角色
- 或动态,根据他们的职责。RBAC在云和企业系统中具有广泛的商业用途,是一种易于理解的工具,可用于管理对物联网设备及其生成的数据的访问。
- 防篡改和检测:此功能在设备和雾网络级别特别重要,但也扩展到核心网络级别。所有这些级别都可能涉及物理上位于受物理安全措施保护的企业区域之外的组件。
- 数据保护和机密性:这些功能扩展到架构的所有级别。
- 互联网协议保护:保护移动中的数据免受窃听和窥探是所有级别之间必不可少的。
图13.12映射了跨物联网模型四层的特定安全功能区域。[FRAH15]还提出了一个安全的物联网框架,该框架定义了物联网安全设施的组件,包括所有级别,如图13.13所示。这四个组成部分是:
- 身份验证:包括通过首先识别物联网设备来启动访问确定的元素。典型的企业网络设备可以通过人工凭证(例如,用户名和密码或令牌)来识别,而物联网端点必须通过不需要人工交互的方式进行指纹识别。这些标识符包括RFID、x.509证书或端点的MAC地址。
- 授权:控制设备在整个网络结构中的访问权限。此元素包含访问控制。它与认证层一起建立必要的参数,以实现设备之间以及设备与应用平台之间的信息交换,并实现与物联网相关的服务。
- 网络强制策略:包括在基础设施上安全地路由和传输端点流量的所有元素,无论是控制、管理还是实际数据流量。
- 安全分析,包括可见性和控制:该组件包括物联网设备中央管理所需的所有功能。首先,这涉及到物联网设备的可见性,这仅仅意味着中央管理服务可以安全地感知分布式物联网设备集合,包括每个设备的身份和属性。建立在这种可见性之上的是施加控制的能力,包括配置、补丁更新和威胁对策。
与此框架相关的一个重要概念是信任关系。在这种情况下,信任关系是指交换的两个伙伴对对方的身份和访问权有信心的能力。信任框架的身份验证组件提供了基本级别的信任,并通过授权组件对其进行扩展。[FRAH15]给出了一个例子,一辆汽车可能与来自同一供应商的另一辆汽车建立信任关系。然而,这种信任关系可能只允许汽车交换它们的安全能力。当同一辆车与其经销商网络之间建立信任关系时,汽车可能被允许共享额外的信息,如里程表读数和上次维护记录。
An Open-source IoT Security Module
This section provides an overview of MiniSec, an open-source security module that is part of the TinyOS operating system. TinyOS is designed for small embedded systems with tight requirements on memory, processing time, real-time response, and power consumption. TinyOS takes the process of streamlining quite far, resulting in a very minimal OS for embedded systems, with a typical configuration requiring 48 KB of code and 10 KB of RAM [LEVI12]. The main application of TinyOS is wireless sensor networks, and it has become the de facto OS for such networks. With sensor networks the primary security concerns relate to wireless communications. MiniSec is designed to be a link-level module that offers a high level of security, while simultaneously keeping energy consumption low and using very little memory [LUK07]. MiniSec provides confidentiality, authentication, and replay protection.
MiniSec has two operating modes, one tailored for single-source communication, and another tailored for multi-source broadcast communication. The latter does not require per-sender state for replay protection and thus scales to large networks.
MiniSec is designed to meet the following requirements:
- Data authentication: Enables a legitimate node to verify whether a message originated from another legitimate node (i.e., a node with which it shares a secret key) and was unchanged during transmission.
- Confidentiality: A basic requirement for any secure communications system.
- Replay protection: Prevents an attacker from successfully recording a packet and replaying it at a later time.
- Freshness: Because sensor nodes often stream time-varying measurements, providing guarantee of message freshness is an important property. There are two types of freshness: Strong and weak. MiniSec provides a mechanism to guarantee weak freshness, where a receiver can determine a partial ordering over received messages without a local reference time point.
- Low energy overhead: This is achieved by minimizing communication overhead and by using only symmetric encryption.
- Resilient to lost messages: The relatively high occurrence of dropped packets in wireless sensor networks requires a design that can tolerate high message loss rates.
CRYPTOGRAPHIC ALGORITHMS Two cryptographic algorithms used by MiniSec are worth noting. The first of these is the encryption algorithm Skipjack. Skipjack was developed in the 1990s by the U.S. National Security Agency (NSA). It is one of the simplest and fastest block cipher algorithms, which is critical to embedded systems. A study of eight possible candidate algorithms for wireless security networks [LAW06] concluded that Skipjack was the best algorithm in terms of code memory, data memory, encryption/decryption efficiency, and key setup efficiency.
Skipjack makes use of an 80-bit key. It was intended by NSA to provide a secure system once it became clear that DES, with only a 56-bit key, was vulnerable. Contemporary algorithms, such as AES, employ a key length of at least 128 bits, and 80 bits is generally considered inadequate. However, for the limited application of wireless sensor networks and other IoT devices, which provide large volumes of short data blocks over a slow data link, Skipjack suffices. With its efficient computation and low memory footprint, Skipjack is an attractive choice for IoT devices.
The block cipher mode of operation chosen for MiniSec is the Offset Codebook (OCB) mode. As mentioned in Chapter 2, a mode of operation must be specified when a plaintext source consists of multiple blocks of data to be encrypted with the same encryption key. OCB mode is provably secure assuming the underlying block cipher is secure. OCB mode is a one-pass mode of operation making it highly efficient. Only one block cipher call is necessary for each plaintext block, (with an additional two calls needed to complete the whole encryption process). OCB is especially well suited for the stringent energy constraints of sensor nodes.
A feature that contributes significantly to the efficiency of OCB is that with one pass through the sequence of plaintext blocks, it produces a ciphertext of equal length and a tag for authentication. To decrypt a ciphertext, the receiver performs the reverse process to recover the plaintext. Then, the receiver ensures that the tag is as expected. If the receiver computes a different tag than the one accompanying the ciphertext, the ciphertext is considered to be invalid. Thus, both message authentication and message confidentiality are achieved with a single, simple algorithm. OCB will be described in Chapter 21.
MiniSec employs per-device keys; that is, each key is unique to a particular pair of devices to prevent replay attacks.
OPERATING MODES MiniSec has two operating modes: Unicast (MiniSec-U) and broadcast (MiniSec-B). Both schemes use OCB with a counter, known as a nonce, that is input along with the plaintext into the encryption algorithm. The least significant bits of the counter are also sent as plaintext to enable synchronization. For both modes, data are transmitted in packets. Each packet includes the encrypted data block, the OCB authentication tag, and the MiniSec counter.
MiniSec-U employs synchronized counters, which require the receiver to keep a local counter for each sender. The strictly monotonically increasing counter guarantees semantic confidentiality.1 Even if the sender A repeatedly sends the same message, each ciphertext is different because a different counter value is used. In addition, once a receiver observes a counter value, it rejects packets with an equal or smaller counter value. Therefore, an attacker cannot replay any packet that the receiver has previously received. If a number of packets are dropped, the sender and receiver engage in a resynchronization protocol.
MiniSec-U cannot be directly used to secure broadcast communication. First, it would be too expensive to run the counter resynchronization protocol among many receivers. In addition, if a node was to simultaneously receive packets from a large group of sending nodes, it would need to maintain a counter for each sender, resulting in high memory overhead. Instead, it uses two mechanisms, a timing-based approach and a bloom-filter approach, that defend against replay attacks. First, the time is divided into t-length epochs E1,E2,.... Using the current epoch or the previous epoch as nonce for OCB encryption, the replay of messages from older epochs is avoided. The timing approach is augmented with a bloom-filter approach in order to prevent replay attacks inside the current epoch. MiniSec-B uses as nonce element in OCB encryption and bloom-filter key the string nodeID.Ei.Cab, where nodeID is the sender node identifier, Ei is the current epoch, and Cab is a shared counter. Every time that a node receives a message, it checks if it belongs to its bloom filter. If the message is not replayed, it is stored in the bloom filter. Else, the node drops it.
For further details on the two operating modes, see [TOBA07].
开源物联网安全模块
本节提供miniec的概述,miniec是TinyOS操作系统的一部分,是一个开源安全模块。TinyOS专为对内存、处理时间、实时响应和功耗要求严格的小型嵌入式系统而设计。TinyOS在精简过程中走得相当远,为嵌入式系统提供了一个非常小的操作系统,典型配置需要48 KB的代码和10 KB的RAM [LEVI12]。TinyOS的主要应用是无线传感器网络,它已经成为这类网络事实上的操作系统。对于传感器网络,主要的安全问题与无线通信有关。MiniSec被设计为提供高级别安全性的链路级模块,同时保持低能耗和使用很少的内存[LUK07]。 MiniSec提供机密性、身份验证和重放保护。
MiniSec有两种工作模式,一种适合单源通信,另一种适合多源广播通信。后者不需要每个发送者状态来进行重放保护,因此可以扩展到大型网络。
MiniSec的设计满足以下要求:
- 数据认证:允许合法节点验证消息是否来自另一个合法节点(即与其共享密钥的节点),并且在传输过程中是否未更改。
- 保密性:任何保密通信系统的基本要求。
- 重放保护:防止攻击者成功记录数据包并在以后的时间重放。
- 新鲜度:由于传感器节点经常流时变测量,提供消息新鲜度的保证是一个重要的属性。新鲜度有两种:强的和弱的。MiniSec提供了一种保证弱新鲜度的机制,接收器可以在没有本地参考时间点的情况下确定接收到的消息的部分排序。
- 低能量开销:这是通过最小化通信开销和仅使用对称加密来实现的。
- 对丢失消息的弹性:无线传感器网络中相对较高的丢包发生率要求设计能够容忍高消息损失率。
加密算法 MiniSec使用的两种加密算法值得注意。第一个是加密算法Skipjack。Skipjack是上世纪90年代由美国国家安全局(NSA)开发的。它是最简单、最快的分组密码算法之一,对嵌入式系统至关重要。对无线安全网络的八种可能候选算法的研究[LAW06]得出结论,Skipjack在代码内存、数据内存、加密/解密效率和密钥设置效率方面是最好的算法。
Skipjack使用80位的密钥。一旦发现只有56位密钥的DES易受攻击,NSA打算提供一个安全的系统。现代的算法,如AES,使用至少128位的密钥长度,80位通常被认为是不够的。然而,对于无线传感器网络和其他物联网设备的有限应用,在缓慢的数据链路上提供大量的短数据块,Skipjack就足够了。凭借高效的计算和低内存占用,Skipjack是物联网设备的一个有吸引力的选择。
miniec选择的分组密码操作模式是偏移码本(OCB)模式。如第2章所述,当明文源由多个要用相同加密密钥加密的数据块组成时,必须指定操作模式。假设底层分组密码是安全的,OCB模式可以证明是安全的。OCB模式是一种操作模式,使其效率很高。对于每个明文块,只需要进行一次分组密码调用(完成整个加密过程还需要另外两次调用)。OCB特别适合于传感器节点的严格能量约束。
对OCB的效率有显著贡献的一个特性是,通过一个明文块序列,它产生一个长度相等的密文和一个用于身份验证的标记。为了解密密文,接收方执行相反的过程来恢复明文。然后,接收方确保标签符合预期。如果接收方计算出的标签与密文附带的标签不同,则认为该密文无效。因此,消息身份验证和消息机密性都是通过一个简单的算法实现的。OCB将在第21章中描述。
MiniSec使用每个设备密钥;也就是说,为了防止重放攻击,每个密钥对特定的设备都是唯一的。
工作模式 MiniSec有单播(MiniSec- u)和广播(MiniSec- b)两种工作模式。这两种方案都使用OCB和计数器(称为nonce),该计数器与明文一起输入到加密算法中。计数器的最低有效位也作为明文发送,以启用同步。对于这两种模式,数据都以数据包的形式传输。每个包包括加密的数据块、OCB身份验证标记和MiniSec计数器。
miniec - u采用同步计数器,它要求接收方为每个发送方保留一个本地计数器。严格单调递增的计数器保证了语义机密性即使发送方A重复发送相同的消息,每个密文也是不同的,因为使用了不同的计数器值。此外,一旦接收方观察到计数器值,它会拒绝计数器值相等或更小的数据包。因此,攻击者不能重放接收方以前收到的任何数据包。如果丢弃了大量的数据包,发送方和接收方就会进行重新同步协议。
mini - u不能直接用于保证广播通信的安全。首先,在许多接收器之间运行计数器重同步协议的成本太高。此外,如果一个节点要同时从一大组发送节点接收数据包,则需要为每个发送方维护一个计数器,这将导致较高的内存开销。相反,它使用两种机制,一种基于时间的方法和一种bloom-filter方法来防御重放攻击。首先,将时间划分为t长度的E1,E2,....使用当前纪元或前一个纪元作为OCB加密的起始点,可以避免重播来自旧纪元的消息。为了防止当前纪元内的重放攻击,该定时方法与bloom-filter方法进行了增强。miniec - b使用字符串nodeID.Ei作为OCB加密和bloom-filter密钥中的nonce元素。Cab,其中nodeID是发送方节点标识符,Ei是当前纪元,Cab是共享计数器。每当节点接收到消息时,它都会检查该消息是否属于其bloom过滤器。如果不重播消息,则将其存储在布隆过滤器中。否则,节点丢弃它。
有关这两种工作模式的详细信息,请参阅[TOBA07]。